Methods
Confidentiality-Preserving Security Assurance is drawing upon a a range of research methods. Jointly, they are forged into an approach to certify the topology of complex systems and enable provers to convince verifiers of the security properties of the topology while keeping the blueprint and sensitive information of the topology confidential.
In general, this project is based on the paradigm to consider system topologies in the form of a graph representation. This representation is formulated by an auditor of the system, who computes a digital signature on the graph. This topology certification in form of the graph signature then enables the system provider to convince other parties, so called verifiers, that certain security properties of the topology are fulfilled, without disclosing its blueprint or other sensitive details.
Topology
The Cambridge Dictionary defines topology as "the way the parts of something are organized or connected." This general meaning is already useful for the understanding of CASCAde. In general, we consider how systems are organized or connected.
Classically, a network topology represents the arrangement of components (nodes, links,...) of a communication network. In such a representation, a device attached to the network is called a node. Nodes can be connected by different means, for instance by a local area network (LAN). The network topology then is an abstraction of the pattern of these inter-connections.
Similarly, the topology of a virtualized infrastructure represents the arrangement of components in a virtualized system. Beyond the network connections themselves (which can be physical wires or virtual LANs (VLANs)), other organizational properties can be modelled. For example, hierarchical connections can represent that a virtual machine is hosted on a particular hypervisor.
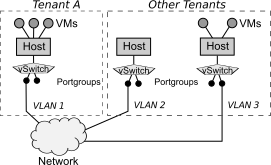
In this figure, we represent VMs, hosts, vSwitches, Portgroups and a network abstraction as vertices. The edges here represent VLAN connections as well as hierarchical associations between hosts and their VMs. Network connections are labeled with their VLAN ID.
Relationship to Topology Certification
While the concept of a topology is dependent on the system paradigm in question, all topologies have in common that they can be represented by graph data structures. Given as a graph representation, topologies can be certified with the help of graph signatures. This kind of topology certification has been first proposed by Groß in 2014.
Graph Representations
A graph is a mathematical datastructure that represents objects that are in some sense related to eachother. It organizes nodes (called vertices, V), their connections (called edges, E) and auxiliary attributes of nodes as well as connections (called labels, L). A graph can be directed or undirected.
A graph representation of a topology formalizes and encodes how entities are connected and organized. For instance, for a virtualized infrastructure topology a graph representation could model the hypervisors, virtual machines, storage nodes, and network switches as vertices. It would then represent the virtual LAN connections, associations between virtual machines and hypervisors, connections to storage systems as edges.
Furthermore, the different elements of the graph can be labeled to represent details of the topology. For example, physical machines and hypervisors could be labeled with their geo-location. (Virtual) machines could be labeled with their operating system version. Edges could be classified by what the edge represents (e.g., a VLAN connection).
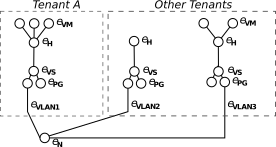
A graph representation such as the one depicted here makes the main ingredient for a graph signature scheme.




